In this post, we will solve the SharePoint Health Analyzer Issue “Accounts used by application pools or service identities are in the local machine Administrators group” in SharePoint 2019 and 2016.
-
1
Accounts used by application pools or service identities are in the local machine Administrators group
- 1.1 Cause
-
1.2
How to solve Accounts used by application pools or service identities are in the local machine Administrators group?
- 1.2.1 List Services that are currently running as accounts in the machine administrators
- 1.2.2 Remove service account of the application pools/services from the local administrator group
- 1.2.3 Remove service account of the application pools/services from the farm administrator group
- 1.2.4 Configure Service Accounts in SharePoint
- 1.2.5 Reanalyze Health Analyzer
Applied To
- SharePoint 2019.
- SharePoint 2016.
- SharePoint 2013.
- SharePoint 2010.
Accounts used by application pools or service identities are in the local machine Administrators group
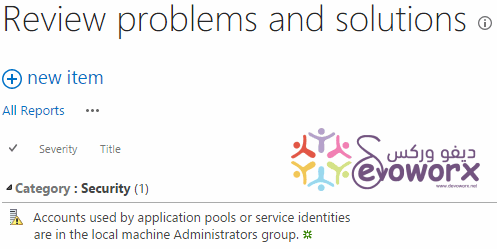
In SharePoint 2016 / 2013 Central Administration, I observed that the Health Analyzer raised the below security warning

I clicked on “View These Issues” link, to check the list of critical issues that have detected by the SharePoint health analyzer, and I had noticed that one of theses issue that listed under the “Security” category was “Accounts used by application pools or service identities are in the local machine Administrators group“
Cause
Before we getting started to fix the “Accounts used by application pools or service identities are in the local machine Administrators group” issue, we should first be aware of the following:
The service account that used to run the Application Pools or SharePoint Services
- Must be a domain user account.
- Must not be a member of the Local Administrators Group on the local machine.
- Shouldn’t be a member of Farm Administrators Group.
Note: Although the issue description informs that the Accounts used by application pools or services are in the local administrator group and it didn’t mention the Farm Administrator Group. but based on Microsoft advise it’s recommended to remove the account from Farm Administrator Group because of using highly privileged accounts for application pools or services poses a security risk to the farm, and could allow malicious code to execute.
Therefore, to avoid raising Accounts used by application pools or services are in the local administrator group in the SharePoint Health analyzer list, you must remove these accounts from the Local Administrator Group and Farm Administrator Group.
Note: Adding the Farm Account to Local Administrator Group is required only to start the User Profile Synchronization Service.
Once the User Profile Synchronization Service is started, you should remove the Farm Account from the Local Administrators group to avoid raising this security warning in Health Analyzer.
For more details, please check SharePoint User Profile Synchronization Service Stuck on Starting and User Profile Synchronization Service Starting then Stopped
How to solve Accounts used by application pools or service identities are in the local machine Administrators group?
To avoid raising this warning “Accounts used by application pools or service are in the local administrator group” in Health Analyzer, we will go through the following:
- List Services that are currently running as accounts in the machine administrators.
- Remove the service account of the application pools/services from the local administrator group.
- Remove the service account of the application pools/services from the farm administrator group.
- Configure Service Accounts.
- Reanalyze the health analyzer issues.
It’s also strongly recommended to read SharePoint 2019: Service Accounts Recommendations.
List Services that are currently running as accounts in the machine administrators
To solve “Accounts used by application pools or service are in the local administrator group“, we should remove the current service account of the application pool/service from the local administrator group and farm administrators group by doing the following:
Steps
- In Health Analyzer, Click on the issue item to check its details.
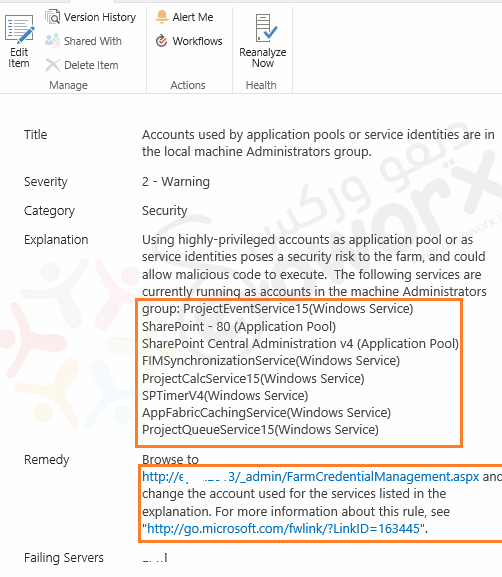
- In Explanation Section, Check the list of application pool or service that running as accounts in the machine administrator group.
- In my case, I have the following application pools and services:
- ProjectEventService15(Windows Service).
- SharePoint – 80 (Application Pool).
- SharePoint Central Administration v4 (Application Pool).
- FIMSynchronizationService(Windows Service).
- ProjectCalcService15(Windows Service).
- SPTimerV4(Windows Service).
- AppFabricCachingService(Windows Service).
- ProjectQueueService15(Windows Service).
- In my case, I have the following application pools and services:
- Now list the corresponding account for each service as the following:
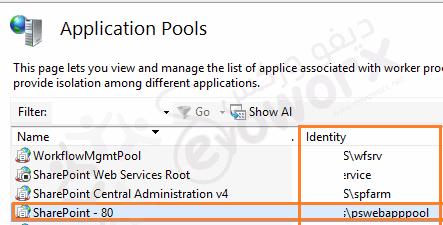
- Regarding Application Pools accounts:
- Open IIS > Application Pool > Below Identity.
- Check the service account related to the application pool that listed in the health analyzer issue.
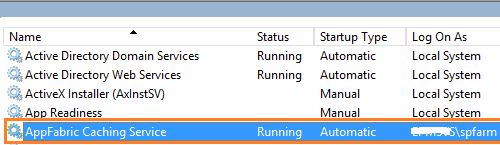
- Regarding Windows Service accounts
- Run “services.msc” to open Services on the server.
- Below “Log on As”, Check the related service account to the application pool that has already listed in the health analyzer issue.
You can also find the the corresponding service account for each application pool or service by going to
- Go to Central Administration > Security > Configure Service Accounts.
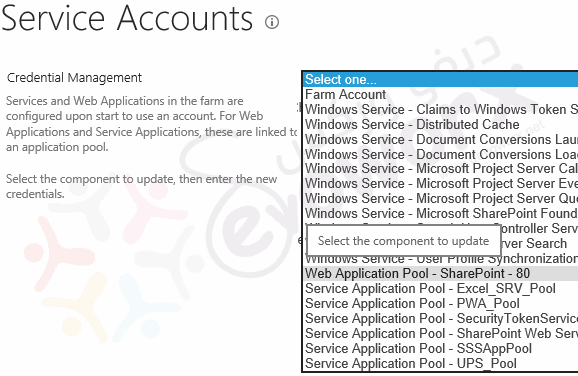
Although this method lists most of the services and Application pools, in some cases the service name in the health analyzer explanation section may be different than that is listed in the Configure Service Accounts list. Eg: AppFabricCachingService is corresponding to a Distributed Cache in Configure Service Accounts.
Also, there are some windows services like SPTimerV4 (Windows Service) mentioned in the Health analyzer issue but it’s not listed in the list component.
Remove service account of the application pools/services from the local administrator group
Once you got all the corresponding service accounts, you should now remove these accounts from Local Administrator Group as the following:
Steps
- Open Server Manager > Tools > Computer Management.
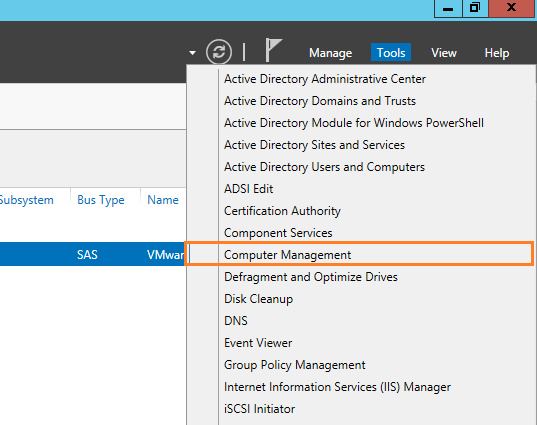
- From left side > Select Local User and Groups > Click on Groups > Administrator Group.
- Right Click on Group name > Properties > From Member tab > select the service account > Remove the account.
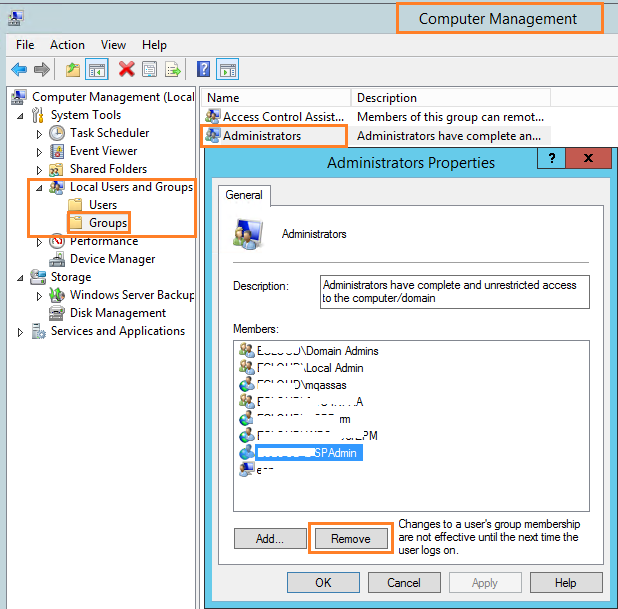
- Repeat the previous steps on all SharePoint Servers that running this service.
Note: After making changes to the farm account, you must restart the SharePoint Timer service or restart the server. This ensures that every SharePoint service that is currently running as the farm account is using the latest credentials.
For more details, Please check Start and Stop SharePoint Service Application using PowerShell
Remove service account of the application pools/services from the farm administrator group
As per Microsoft recommendations, it’s recommended to remove the application pool /service account from the farm administrator group because using highly privileged accounts for application pools or services poses a security risk to the farm, and could allow malicious code to execute.
Therefore, you should also delete the service account from the farm administrator group by following the below steps:
Steps
- Open Central Administration > Security > Manage the farm administrators group
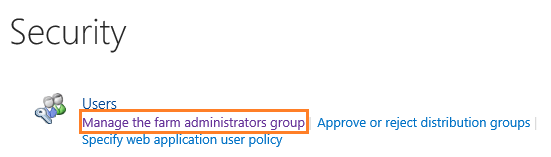
- Check the service account > From Actions menu > Remove.
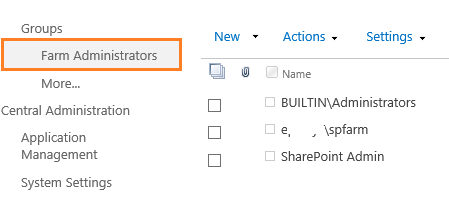
Note: You can’t remove the farm account from the farm administrators group.
You might also like to read Local administrator privilege is required to update the Farm Administrators’ group
In this step, we’ll perform a quick review for all service accounts that used by all Application Pools and Services in SharePoint farm, Also we will make sure that theses accounts is not listed in the Local Administrator Group for all SharePoint servers cross the farm.
- Go to Central Administration > Security > Configure Service Accounts.
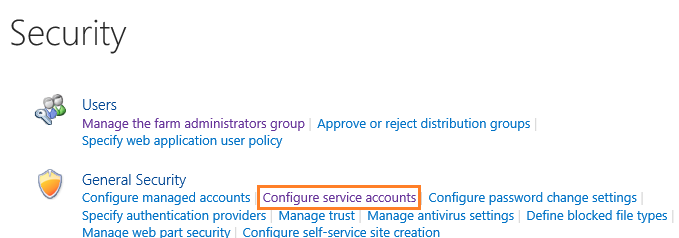
- On the Service Accounts page > Select the application pool or service that is already running as an account in local administrator group.

- In the “Select an account“ list, Make sure that the selected account is not added to the local administrator group.
Notes to Configure Service Accounts
When use the SharePoint Central Administration to configure Service Account, you should be aware of the following points:
- There are some windows services like SPTimerV4 (Windows Service) that may be mentioned in the Health analyzer issue but it’s not listed in the list component.
- Also, there are some services with a different name like AppFabricCachingService (Windows Service) that corresponding to the Distributed Cache in the component list.
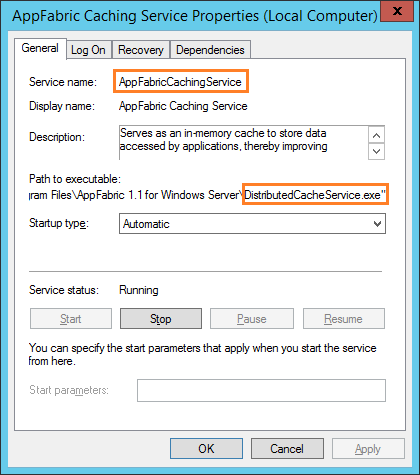
- Moreover, there are services like Distributed Cache Service that does not support changing its service account from Central Administration, and to change the distributed cache service account you should use PowerShell as we mentioned at Distributed Cache Service does not support this operation from Central Administration. Please use Sharepoint Powershell command lets.

- The SharePoint Central Administration and SharePoint Timer Service must be running used Farm Account.
- The “SPSearchHostController” windows service needs to run as the farm admin in order to start Search Service.
- For the other services, It’s recommended to use one service account for all Service Applications. There’s no reason to use multiple service accounts that will just consume memory and slow down startup time.
- Not all accounts should be registered as a managed account, read more at SharePoint 2019: Register Managed Account using PowerShell.
- It’s also recommended to read SharePoint 2019: Service Accounts Recommendations.
Reanalyze Health Analyzer
Once you have performed the above steps and instructions, you should now Reanalyze the health analyzer issue to make sure the issue has been solved by doing the following:
Steps
- Open Central Administration > Monitoring > Review problems and solutions.
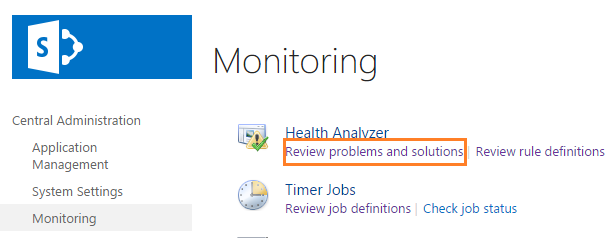
- Click on the error > From the above ribbon > Select the Reanalyze Now.
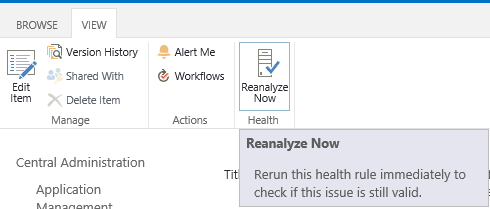
- Wait a moment, then go back to the Health analyzer report list, you will note that the “Accounts used by application pools or service are in the local administrator group” is gone and not listed as a critical issue in the Health Analyzer.
Conclusion
In conclusion, we have explained step by step how we can solve the “Accounts used by application pools or service are in the local administrator group” that raised in SharePoint Health Analyzer list.
You might also like to read
- Product/patch installation or server upgrade required.
- Missing server side dependencies issue within Health Analyzer in SharePoint Server 2013.
- Database running in compatibility range upgrade recommended.
- The operation cannot be performed on database because it is involved in a database mirroring.
- InfoPath Forms Services forms cannot be filled out in a Web browser because no State Service connection is configured.
- A State Service Application has no database defined.
Have a Question?
If you have any related questions, please don’t hesitate to Ask it at deBUG.to Community.

Pingback: SharePoint 2019: Service Accounts Recommendations | SPGeeks
Great article as always
Thanks for your great article here. After I read your tips here, now I knew what I have to do with this issue.